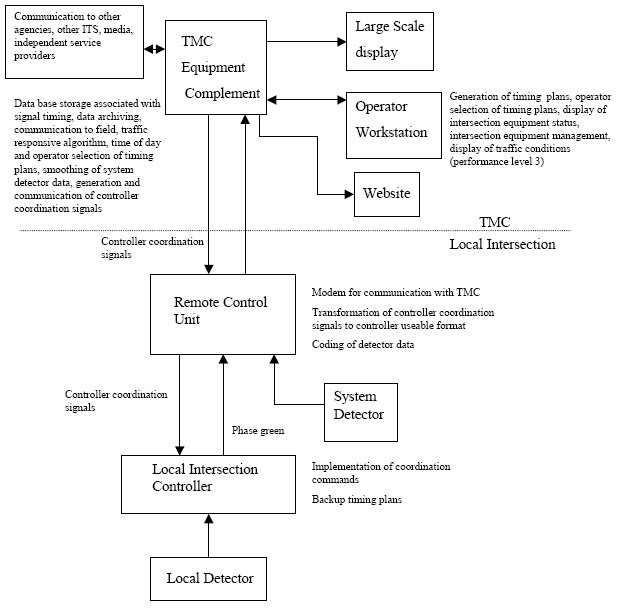
The smart Trick of Security Bollards That Nobody is Talking About
The finish you select will possibly be notified by your setup area front-of-house bollards tend not to be just galvanized steel or plain concrete, for example. Usual options are: a nice, high-polish surface that adds a touch of design without sacrificing energy. An excellent choice for public or consumer parking area, around the front of your structure, above roads and other locations where the appearance of the bollard is important.
Powder-coating is a terrific alternative where the bollard needs to be eye-catching. You will certainly need to make sure that the repainted coating on these blog posts is preserved to ensure that corrosion does not take hold.

The 9-Minute Rule for Security Bollards
They play an useful role in avoiding access to lorries and employees when it is hazardous or forbidden. While a bollard might appear easy at initial glimpse, over the years these tools have actually advanced and branched out with different tools to match several various niches.
These brightly coloured bollards are created to stand out and drift traffic, instead of create an impervious obstacle. Plastic bollards are generally made with a procedure called shot moulding. This procedure entails heating plastic pellets to a high temperature and after that putting them into a bollard-shaped mould. These bollards are not installed, rather they are developed to be lightweight and movable for momentary circumstances.
These bollards are commonly produced via a procedure called milling in which wood is travelled through an equipment that utilizes blades to suffice into a preferred shape. When installing wooden bollards, a hole will typically be mined the wooden bollard to go into, before it is then safeguarded making use of concrete.
At Workplace Pedestrian Security, we offer a costs customized concrete bollard service. Concrete bollards are produced by mixing concrete and putting it right into a specially created mould.
The Best Guide To Security Bollards
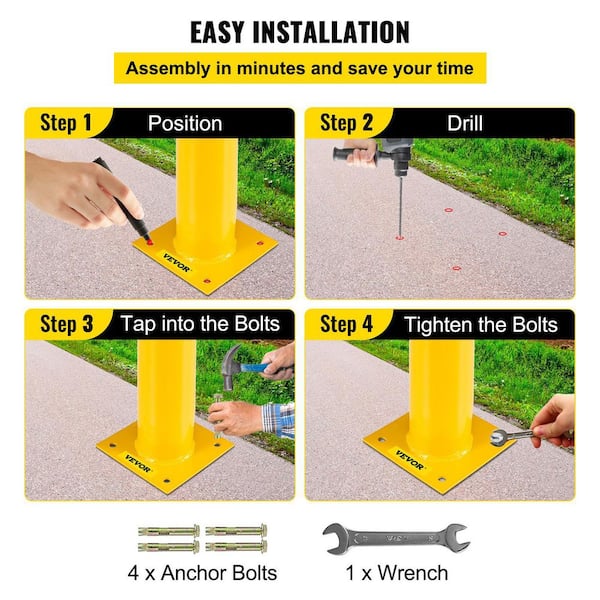
If you have an interest in custom concrete bollards or any of our various other services, after that connect with our specialist team today.
Removable: (quite a solid sort of Post, no fret about below ground solutions when suitable & popular as both Parking Deterrent or Safety and security along with excellent worth for cash). Fully Telescopic: (these are by far the strongest sort of Article or Bollard offered, the principle is that there is even more material underground as opposed to what is over ground, they do take even more time for the installation however the first option for Safety and security).
Removable & Telescopic Posts & Bollards leave a flush ground finish when not in use, the Removable models are stored away from the ground faucet (boot, garage or additional spigot) with a hinged lid completely covering the access hole, the Telescopic versions move right into the ground leaving a totally flush finish, both resulting in No Trip Dangers perfect for places with Public Accessibility or locations where you have very low Autos or limited gain access to making it essential to drive over the Article.
Security Bollards for Dummies
The items are likewise referred as: Parking lot Poles. Steel Driveway Posts. Driveway Poles. Anti-theft Steel Poles. Drive Posts. Driveway Posts. Drive Entryway Posts & Bollards. Go down Down Bollards & Auto Parking Posts. Is the area of the post going to have low framework cars or bikes driving over them or probably tight access significance that you need to drive over the place of the Post, or are they situated where the basic public or staff may be strolling over them? A Layer Down Post or Bollard will lay on the ground when not in use, for the large majority of applications this does not trigger a trouble since they get on private ground and the owners can make certain that there lorries will certainly have the ability to safely drive over the message they have picked.